Earlier this week, a Ukrainian security researcher expired nearly two years of internal log files for chat Conti, one of the most predatory and ruthless ransom gangs operating today. Tuesday’s story looks at how Conti handles its own internal breakthroughs and attacks by private security companies and governments. In Part II of this series, we will look at what it’s like to work for Conti, as described by Conti employees themselves.

The Conti group’s chats reveal a lot about its internal structure and hierarchy. Conti maintains many of the same business units as a legitimate, small to medium-sized enterprise, including a human resources department responsible for continuously interviewing potential new employees.
Other Conti departments with their own separate budgets, staffing schedules and senior management include:
–Encoders: Programmers hired to write malicious code to integrate different technologies
–Testers: Employees responsible for testing and closing Conti malware against security tools
–Administrators: Workers tasked with setting up, crashing servers, other attack infrastructure
–Reverse engineers: Those who can disassemble computer code, study it, find vulnerabilities or weaknesses
–Penetration Testers / Hackers: Those at the forefront who fight corporate security teams to steal data and plant ransom software.
Conti seems to have negotiated much of its spam operations, or at least no mention of “spammers” as direct employees. Conti leaders seem to have set tight budgets for each of their organizational units, although it occasionally borrows from one department to meet the urgent cash flow needs of another.
Many of the most revealing chats about Conti’s structure are betweenmango“- a mid-level Conti manager to whom many other Conti employees report every day – and”Stern“, Something like a grumpy supervisor who can be seen to be constantly annoyed by staff for reporting on their work.
In July 2021, Mango told Stern that the group was running ads on several Russian-language cybercrime forums to hire more workers. “The salary is $ 2k in the message, but there are many comments that we are recruiting slaves to galleys,” wrote Mango. “Of course, we dispute this and say that those who work and give results can earn more, but there are examples of coders who work normally and earn $ 5- $ 10k salary.
Conti’s chats show that the gang mainly monitors victims’ bots infected with their malware, both through Trickboat and Emotet criminal software platforms as a service and that it has hired dozens of people to continuously test, maintain and expand this infrastructure 24 hours a day, 7 days a week.
Conti members call Emotet “Buz“or”Buza”, And it is obvious from reading these chat logs that Buza had its own stable of more than 50 coders and probably much of the same organizational structure as Conti.
According to Mango, as of July 18, 2021, the Conti gang has hired 62 people, mostly low-level malware encoders and software testers. However, the list of Conti employees seems to have fluctuated greatly from month to month. For example, the organization has repeatedly been forced to lay off many employees as a precautionary measure after its own internal security breaches.
In May 2021, Stern told Mango that he wanted his subordinates to hire another 100 “encoders” to work with the group’s malware before most of the gang returned from their summer vacations in the Crimea. Most of these new employees, Stern says, will join the intrusion / hacking testing teams led by Conti leaders.Hof“and”Reverse“Both Hof and Reverse appear to have direct access to the Emotet crime software platform.
Attempts to estimate the exact size of Conti’s organization are problematic, in part because cybersecurity experts have long believed that Conti is simply a rebrand to another strain of ransomware and an affiliate program known as Ryuk. First spotted in 2018, Ryuk was just as ruthless and mercenary as Conti, and the FBI says Ryuk earned more than $ 61 million in ransom in his first year.
“Conti is a target version of Ryuk that comes from Trickbot and Emotet, which we’ve been watching for some time,” researchers at Palo Alto Networks wrote for Ryuk last year. “A strong focus was placed on hospital systems, probably due to the need for time to work, as these systems were overloaded by dealing with the ongoing COVID-19 pandemic. We have seen Ryuk’s initial ransom demands ranging from $ 600,000 to $ 10 million in a number of industries.
On 14 May 2021 in Ireland Executive Director of the Health Service (HSE) suffered a major ransomware attack from Conti. The attack will disrupt services in several Irish hospitals and lead to an almost complete shutdown of HSE’s national and local networks, forcing the cancellation of many outpatient clinics and health services. It took HSE until September 21, 2021, to fully recover all of its systems from the attack, at an estimated cost of over $ 600 million.
From reading these chats, it remains unclear how many Conti employees have realized how many of the organization’s operations overlap with Ryuk’s. Lawrence Abrams in Bleeping Computer mentioned Conti’s chat from October 2020, in which the representative of Emotet “Buza” published a link to the analysis of a security company for the return of Ryuk.
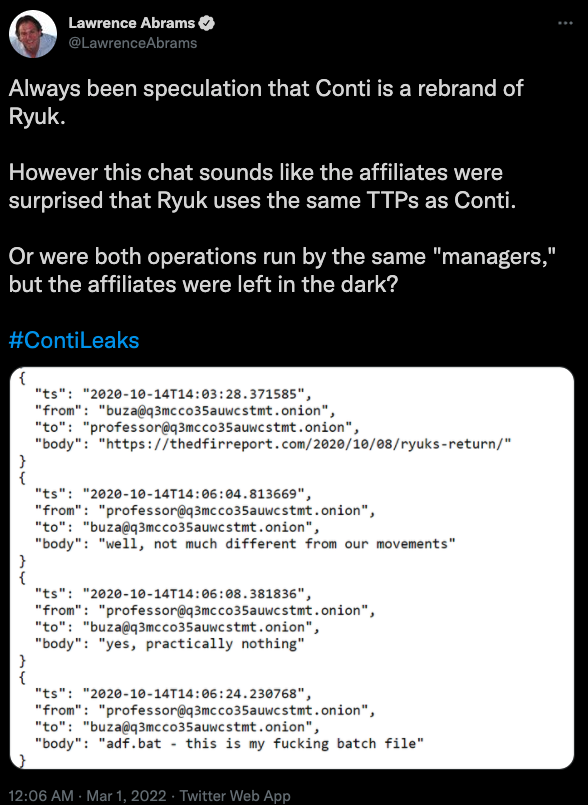
“Professor“The nickname chosen by one of Conti’s top generals is that Ruck’s tools, techniques and procedures are almost identical to Conti’s.
“Adf.bat is my fucking batch file,” wrote a professor, apparently surprised to read the analysis and notice that his own code was being reused in high-profile Ryuk ransomware attacks.
“It feels like [the] the same managers managed both Ryuk and Conti, with a slow migration to Conti in June 2020. ”, Abrams wrote on Twitter. “However, based on chats, some affiliates did not know that Ryuk and Conti were run by the same people.”
DELETE
Each Conti employee was assigned a specific 5-day work week, and staff schedules were distributed so that a number of employees were always available 24/7 to deal with technical problems with the botnet or to respond to ransom negotiations initiated by victim organization.
Like countless other organizations, Conti makes its payroll on the 1st and 15th of each month, albeit in the form of bitcoin deposits. Most employees receive payments of $ 1,000 to $ 2,000 a month.
However, many employees used Conti’s chat room to talk about working days without sleep or breaks, while senior managers ignored their repeated requests for rest.
In fact, the diaries show that Conti struggles to maintain a constant number of programmers, testers and administrators in the face of mostly grueling and repetitive work that doesn’t pay very well (especially in terms of the profits of the group’s top management). Moreover, some of the best members of the group were openly approached to work for competing ransomware organizations, and the group’s overall morale seemed to fluctuate between pay days.
Perhaps unsurprisingly, turnover, depletion and burnout were quite high for low-level Conti employees, which means that the group was forced to constantly recruit new talent.
“Our work in general is not difficult, but monotonous, we do the same thing every day,” he wrote.Bentley“, The pseudonym chosen by a key Conti employee who is apparently responsible for” encrypting “the group’s malware – ensuring that it goes unnoticed by all or at least most antivirus products on the market.
Bentley was turning to a new Conti lease – “Idgo“- telling him about his daily duties.
“Basically, that involves running files and checking them according to the algorithm,” Bentley told Idgo. “Investigate communication with the encoder to receive files and send reports to it. Also communication with the cryptor to send the test module to the crypt. Then test the crypt. If congestion occurs at this stage, then send reports to the cryptocurrency and work with it. And as a result – the issuance of the finished crypt to the partner. “
Bentley warned that this testing of their malware should be repeated approximately every four hours to ensure that any new malware detection capabilities added to Windows Defender – Windows’s built-in antivirus and security service – will not interferes with their code.
“A new Defender database update is released approximately every 4 hours,” Bentley told Idgo. “You have to work 8 hours before 20-21 Moscow time. And career development is possible. ” Idgo agrees, noting that he started working for Conti a year earlier as a code tester.

OBSERVATIONS
The recorders show that Conti’s gang is extremely good at quickly finding many potential new victims of ransomware, and the records include a lot of internal debate in Conti’s management about how many certain victim companies should be forced to pay. They also show with terrifying precision how a cleverly large, organized cybercrime group can transform from a single compromised computer to a wholly owned Fortune 500 company.
As a well-equipped “big game” killing machine, Conti may be incomparable to ransomware groups. But internal chat logs show that this group is in dire need of some workflow management and tracking tools. This is because over and over again, the Conti gang has lost control of countless bots – all potential sources of ransom revenue that will help pay employees’ salaries for months – due to a simple omission or mistake.
Conti’s recent chats – approximately several times a week – have highlighted requests from various officials responsible for maintaining the sprawling and ever-changing digital assets that support the ransom group’s operation. These messages invariably refer to overdue invoices for multiple virtual servers, domain registrations, and other cloud-based resources.
On 1 March 2021, a low-level Conti employee named “CarterHe says the bitcoin fund used to pay for VPN subscriptions, antivirus licenses, new servers and domain registrations is less than $ 1,240 in bitcoin.
“Hello, we’re done with bitcoins, four new servers, three vpn subscriptions and 22 renewals have been released,” Carter wrote on November 24, 2021. Two weeks before the $ 960 renewals for bitcoin 0.017. Please send some bitcoins to this wallet, thank you. “
As part of research on this series, KrebsOnSecurity has spent many hours reading every day in Conti’s chats since September 2020. I wish I could get back many of those hours: much of the talk is mind-bogglingly boring chats and store talk . But overall, I was left with the impression that Conti is a very effective – albeit remarkably inefficient – cybercrime organization.
Part of Conti’s disorganized nature is probably endemic in the cybercrime industry, which is of course made up of criminals who are probably accustomed to a less regulated lifestyle. But make no mistake: as redemption teams like Conti continue to increase payouts from victim organizations, there will be growing pressure on these groups to tighten their operations and work more efficiently, professionally and profitably.
Expect Part III of this series, which will look at how Conti provided access to the cyberweapons needed to undermine the security of their targets, and how team leaders approached ransom negotiations with their victims.
